SSS Yet To Be Done.
https://en.wikipedia.org/wiki/Keystroke_logging
| This article is part of a series on |
| Information security |
|---|
| Related security categories |
|---|
|
|
| Threats |
|---|
|
|
| Defenses |
|---|
|
|
|
|
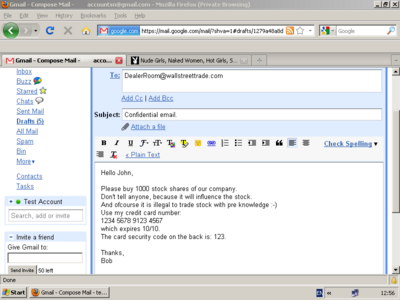
A keylogger example of a screencapture, which holds potentially confidential and private information. The image below holds the corresponding keylogger text result.
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keylogger can be either software or hardware.
While the programs themselves are legal,[1] with many of them being designed to allow employers to oversee the use of their computers, keyloggers are most often used for the purpose of stealing passwords and other confidential information.[2][3]
Keylogging can also be used to study human–computer interaction. Numerous keylogging methods exist: they range from hardware and software-based approaches to acoustic analysis.
Links
See also
Subcategories
``
Pages
`A
Any Keylogger
`S
Spyrix Free Keylogger
Pages in Other Languages
Forking
Categories:
Cryptographic attacks
Spyware
Cybercrime
Security breaches
Comments (0)
You don't have permission to comment on this page.